Dieses Wiki ist ein Archiv bis 2023. Das aktuelle Wiki findet sich unter https://wiki.hamburg.ccc.de/
Difference between revisions of "Freifunk:VPN1"
m |
m |
||
| (32 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | Dieser Node besteht momentan aus | + | {{Veraltet}} |
| + | |||
| + | Dieser Node besteht momentan aus einer virtuellen Maschine unter VMware ESXi und soll die Verbindung zwischen den einzelnen Funkwolken in Hamburg und Freifunk Initiativen in anderen Staedten herstellen. Als VPN Software wird [http://www.tinc-vpn.org/ Tinc-VPN], OpenVPN und n2n eingesetzt. Eine kleine Hilfestellung fuer die VPN Konfiguration auf Basis von OpenWRT kann man hier finden: [[Freifunk:IP:VPN_Connect]] | ||
| + | |||
| + | Es gibt ein Looking Glass im Hamburger Freifunk Netz, das allerdings auch nur aus dem Freifunk Netz erreichbar ist: http://lg.hamburg.freifunk.net/ | ||
| + | |||
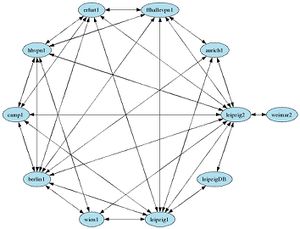
| + | [[Image:InterCity-VPN.jpg|thumb|right|Tinc Connections]] | ||
| Line 11: | Line 17: | ||
Interface Name: eth0 | Interface Name: eth0 | ||
| − | IP Adresse : | + | IP Adresse : 62.206.43.20 |
| − | Hostname : | + | Hostname : vpn1.hamburg.freifunk.net |
| − | Description : | + | Description : uplink |
| − | Bandwidth : | + | Bandwidth : 10mbit up/down |
| + | |||
| − | === | + | === ffhh_tinc === |
| − | + | Dieses Interface ist fuer das Hamburger Freifunk Netz eingerichtet. [http://www.tinc-vpn.org/ Tinc-VPN] setzt dieses Interface in den TAP-Modus, damit Pakete zwischen den einzelnen VPN Clients wie bei einem Switch verschickt werden koennen. Die OLSR und B.A.T.M.A.N. Daemons senden ihre Pakete an die Broadcast-Adresse (10.127.255.255) ueber dieses Interface. | |
| − | Interface Name: | + | Interface Name: ffhh_tinc |
| − | IP | + | IP Adresse : 10.112.1.1/12 |
Hostname : none | Hostname : none | ||
| − | Description : | + | Description : Freifunk Hamburg |
| − | + | Software : tinc-vpn, olsrd | |
| + | Tinc-Port : 656 | ||
| − | === | + | === ffhh_ovpn === |
| − | + | Interface Name: ffhh_ovpn | |
| + | IP Adresse : 10.112.1.3/12 | ||
| + | Hostname : none | ||
| + | Description : Freifunk Hamburg | ||
| + | Software : openvpn, olsrd | ||
| + | OpenVPN-Port : 4223 | ||
| − | + | === ffhh_n2n === | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Interface Name: ffhh_tinc | |
| − | + | IP Adresse : 10.112.1.4/12 | |
| − | |||
| − | |||
| − | |||
| − | Interface Name: | ||
| − | IP Adresse : 10.112.1. | ||
Hostname : none | Hostname : none | ||
Description : Freifunk Hamburg | Description : Freifunk Hamburg | ||
| − | Software : | + | Software : n2n, olsrd |
| − | + | ||
| − | === | + | === icvpn === |
Fuer das [http://wiki.freifunk.net/IC-VPN InterCity-VPN] wurde dieses Interface eingerichtet. [http://www.tinc-vpn.org/ Tinc-VPN] setzt auch dieses Interface in den TAP-Modus und die [http://www.quagga.net Quagga Routing Suite] kuendigt den Hamburger Freifunk IP-Bereich an entfernte BGP-Router. Wir verwenden die interne [http://wiki.freifunk.net/AS-Nummern AS-Nummer] 65044 fuer das BGP-Peering. | Fuer das [http://wiki.freifunk.net/IC-VPN InterCity-VPN] wurde dieses Interface eingerichtet. [http://www.tinc-vpn.org/ Tinc-VPN] setzt auch dieses Interface in den TAP-Modus und die [http://www.quagga.net Quagga Routing Suite] kuendigt den Hamburger Freifunk IP-Bereich an entfernte BGP-Router. Wir verwenden die interne [http://wiki.freifunk.net/AS-Nummern AS-Nummer] 65044 fuer das BGP-Peering. | ||
| − | Interface Name: | + | Interface Name: icvpn |
IP Adresse : 10.207.0.9/16 | IP Adresse : 10.207.0.9/16 | ||
| − | Hostname : | + | Hostname : none |
Description : tunnel staedtekopplung | Description : tunnel staedtekopplung | ||
Software : tinc-vpn, quagga(bgpd) | Software : tinc-vpn, quagga(bgpd) | ||
| Line 62: | Line 66: | ||
== Konfigurationen == | == Konfigurationen == | ||
| + | |||
| + | === OLSRd === | ||
| + | ==== /etc/olsrd-ipv4.conf ==== | ||
| + | |||
| + | <pre> | ||
| + | DebugLevel 2 | ||
| + | IpVersion 4 | ||
| + | FIBMetric "flat" | ||
| + | ClearScreen yes | ||
| + | AllowNoInt yes | ||
| + | |||
| + | Hna4 | ||
| + | { | ||
| + | 0.0.0.0 0.0.0.0 # Default Route to Internet | ||
| + | 10.112.1.255 255.255.255.255 # Looking Glass IP Address | ||
| + | 10.207.0.0 255.255.0.0 # ICVPN Transfer Network | ||
| + | |||
| + | 10.4.0.0 255.252.0.0 # CCC Hamburg ChaosVPN | ||
| + | 10.32.0.0 255.240.0.0 # CCC Hamburg ChaosVPN | ||
| + | |||
| + | 77.87.48.0 255.255.248.0 # Freifunk Berlin public IP range | ||
| + | 191.161.0.0 255.255.0.0 # Freifunk Augsburg | ||
| + | 194.26.180.0 255.255.255.0 # Freifunk Erfurt | ||
| + | |||
| + | 10.2.0.0 255.255.0.0 # Freifunk Hannover | ||
| + | |||
| + | 10.12.0.0 255.255.0.0 # Freifunk Dresden | ||
| + | 10.200.0.0 255.255.0.0 # Freifunk Dresden | ||
| + | |||
| + | 172.22.0.0 255.254.0.0 # dn42.net (aka diac24.net) | ||
| + | |||
| + | 104.0.0.0 255.0.0.0 # BerlinBackBone OLSR Range | ||
| + | 105.0.0.0 255.0.0.0 # BerlinBackBone Batman Range | ||
| + | |||
| + | 10.35.0.0 255.255.0.0 # FCruise Hamburg Datacenter | ||
| + | 91.210.212.0 255.255.255.240 # FCruise Hamburg Transfer Network | ||
| + | 91.210.215.0 255.255.255.0 # FCruise Hamburg testing network | ||
| + | |||
| + | } | ||
| + | |||
| + | |||
| + | # TOS(type of service) value for | ||
| + | # the IP header of control traffic. | ||
| + | # If not set it will default to 16 | ||
| + | |||
| + | #TosValue 16 | ||
| + | |||
| + | # The fixed willingness to use(0-7) | ||
| + | # If not set willingness will be calculated | ||
| + | # dynamically based on battery/power status | ||
| + | # if such information is available | ||
| + | |||
| + | #Willingness 4 | ||
| + | |||
| + | # Allow processes like the GUI front-end | ||
| + | # to connect to the daemon. | ||
| + | |||
| + | IpcConnect | ||
| + | { | ||
| + | MaxConnections 0 | ||
| + | Host 127.0.0.1 | ||
| + | #Net 192.168.1.0 255.255.255.0 | ||
| + | } | ||
| + | |||
| + | UseHysteresis no | ||
| + | #HystScaling 0.50 | ||
| + | #HystThrHigh 0.80 | ||
| + | #HystThrLow 0.30 | ||
| + | |||
| + | |||
| + | LinkQualityLevel 2 | ||
| + | #LinkQualityAging 0.1 | ||
| + | #LinkQualityAlgorithm "etx_fpm" | ||
| + | |||
| + | Pollrate 0.05 | ||
| + | |||
| + | NicChgsPollInt 3.0 | ||
| + | |||
| + | # TC redundancy | ||
| + | # Specifies how much neighbor info should | ||
| + | # be sent in TC messages | ||
| + | # Possible values are: | ||
| + | # 0 - only send MPR selectors | ||
| + | # 1 - send MPR selectors and MPRs | ||
| + | # 2 - send all neighbors | ||
| + | # | ||
| + | # defaults to 0 | ||
| + | |||
| + | TcRedundancy 2 | ||
| + | |||
| + | |||
| + | # | ||
| + | # MPR coverage | ||
| + | # Specifies how many MPRs a node should | ||
| + | # try select to reach every 2 hop neighbor | ||
| + | # | ||
| + | # Can be set to any integer >0 | ||
| + | # | ||
| + | # defaults to 1 | ||
| + | |||
| + | MprCoverage 3 | ||
| + | |||
| + | |||
| + | # Olsrd plugins to load | ||
| + | # This must be the absolute path to the file | ||
| + | # or the loader will use the following scheme: | ||
| + | # - Try the paths in the LD_LIBRARY_PATH | ||
| + | # environment variable. | ||
| + | # - The list of libraries cached in /etc/ld.so.cache | ||
| + | # - /lib, followed by /usr/lib | ||
| + | |||
| + | # Example plugin entry with parameters: | ||
| + | |||
| + | LoadPlugin "olsrd_dot_draw.so.0.3" | ||
| + | { | ||
| + | PlParam "port" "2004" | ||
| + | PlParam "allow" "127.0.0.1" | ||
| + | PlParam "allow" "localhost" | ||
| + | } | ||
| + | |||
| + | LoadPlugin "olsrd_httpinfo.so.0.1" | ||
| + | { | ||
| + | PlParam "port" "8080" | ||
| + | PlParam "net" "0.0.0.0 0.0.0.0" | ||
| + | } | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | Interface "ffhh_tinc" "ffhh_ovpn" "ffhh_n2n" | ||
| + | { | ||
| + | Ip4Broadcast 255.255.255.255 | ||
| + | HelloInterval 2.0 | ||
| + | HelloValidityTime 20.0 | ||
| + | TcInterval 5.0 | ||
| + | TcValidityTime 30.0 | ||
| + | MidInterval 5.0 | ||
| + | MidValidityTime 30.0 | ||
| + | HnaInterval 5.0 | ||
| + | HnaValidityTime 30.0 | ||
| + | } | ||
| + | |||
| + | |||
| + | |||
| + | Interface "n2n" | ||
| + | { | ||
| + | Ip4Broadcast 255.255.255.255 | ||
| + | HelloInterval '50.0' | ||
| + | HelloValidityTime '900.0' | ||
| + | TcInterval '30.0' | ||
| + | TcValidityTime '2700.0' | ||
| + | MidInterval '150.0' | ||
| + | MidValidityTime '2700.0' | ||
| + | HnaInterval '150.0' | ||
| + | HnaValidityTime '900.0' | ||
| + | } | ||
| + | </pre> | ||
| + | |||
| + | ==== /etc/olsrd-ipv6.conf ==== | ||
| + | |||
| + | <pre> | ||
| + | DebugLevel 2 | ||
| + | IpVersion 6 | ||
| + | AllowNoInt yes | ||
| + | Pollrate 0.025 | ||
| + | TcRedundancy 2 | ||
| + | MprCoverage 3 | ||
| + | LinkQualityFishEye 1 | ||
| + | LinkQualityWinSize 100 | ||
| + | LinkQualityDijkstraLimit 0 9.0 | ||
| + | LinkQualityLevel 2 | ||
| + | UseHysteresis no | ||
| + | FIBMetric "flat" | ||
| + | ClearScreen yes | ||
| + | Willingness 3 | ||
| + | LinkQualityAging 0.1 | ||
| + | #LinkQualityAlgorithm "etx_fpm" | ||
| + | LinkQualityAlgorithm "etx_ff" | ||
| + | |||
| + | Hna6 | ||
| + | { | ||
| + | :: 0 # Announce Default Gateway | ||
| + | 2002:3ece:2b14:: 48 # Announce 6to4 prefix | ||
| + | 0:0:0:0:0:FFFF:0:0 96 # Announce siit prefix | ||
| + | 0:0:0:0:0:FFFF:0A70:0101 125 # Announce siit 10.112.1.0-7 | ||
| + | } | ||
| + | |||
| + | |||
| + | IpcConnect | ||
| + | { | ||
| + | MaxConnections 0 | ||
| + | Host 127.0.0.1 | ||
| + | #Net 192.168.1.0 255.255.255.0 | ||
| + | } | ||
| + | |||
| + | NicChgsPollInt 3.0 | ||
| + | |||
| + | |||
| + | LoadPlugin "olsrd_dot_draw.so.0.3" | ||
| + | { | ||
| + | PlParam "port" "2006" | ||
| + | PlParam "allow" "127.0.0.1" | ||
| + | PlParam "allow" "localhost" | ||
| + | } | ||
| + | |||
| + | |||
| + | |||
| + | Interface "ffhh_tinc" "ffhh_ovpn" "ffhh_n2n" | ||
| + | { | ||
| + | Ip6AddrType global | ||
| + | Ip6MulticastGlobal ff0e::1 | ||
| + | HelloInterval 2.0 | ||
| + | HelloValidityTime 40.0 | ||
| + | TcInterval 5.0 | ||
| + | TcValidityTime 100.0 | ||
| + | MidInterval 18.0 | ||
| + | MidValidityTime 324.0 | ||
| + | HnaInterval 18.0 | ||
| + | HnaValidityTime 108.0 | ||
| + | } | ||
| + | |||
| + | |||
| + | Interface "n2n" | ||
| + | { | ||
| + | Ip6AddrType global | ||
| + | Ip6MulticastGlobal ff0e::1 | ||
| + | HelloInterval '50.0' | ||
| + | HelloValidityTime '900.0' | ||
| + | TcInterval '30.0' | ||
| + | TcValidityTime '2700.0' | ||
| + | MidInterval '150.0' | ||
| + | MidValidityTime '2700.0' | ||
| + | HnaInterval '150.0' | ||
| + | HnaValidityTime '900.0' | ||
| + | |||
| + | } | ||
| + | </pre> | ||
| + | |||
=== Tinc-VPN === | === Tinc-VPN === | ||
==== Hamburger Freifunk VPN (ffhh) ==== | ==== Hamburger Freifunk VPN (ffhh) ==== | ||
===== ffhh/tinc.conf ===== | ===== ffhh/tinc.conf ===== | ||
| − | |||
AddressFamily=ipv4 | AddressFamily=ipv4 | ||
Name = vpn1 | Name = vpn1 | ||
| Line 75: | Line 316: | ||
BindToAddress = 62.206.27.20 | BindToAddress = 62.206.27.20 | ||
Hostnames=yes | Hostnames=yes | ||
| − | ConnectTo = vpn2 | + | ConnectTo = lok72 |
| + | ConnectTo = elan | ||
| + | ConnectTo = harburg1 | ||
| + | #ConnectTo = vpn2 | ||
| + | #ConnectTo = cgre | ||
| + | #ConnectTo = Stockholm | ||
| + | |||
===== ffhh/tinc-up ===== | ===== ffhh/tinc-up ===== | ||
| − | |||
#!/bin/sh | #!/bin/sh | ||
ip addr add dev $INTERFACE 10.112.1.1/12 broadcast 10.127.255.255 | ip addr add dev $INTERFACE 10.112.1.1/12 broadcast 10.127.255.255 | ||
| Line 86: | Line 332: | ||
===== ffhh/tinc-down ===== | ===== ffhh/tinc-down ===== | ||
| − | |||
#!/bin/sh | #!/bin/sh | ||
ip link set dev $INTERFACE down | ip link set dev $INTERFACE down | ||
| Line 93: | Line 338: | ||
===== ffhh/hosts/vpn1 ===== | ===== ffhh/hosts/vpn1 ===== | ||
| − | + | Address = vpn1.hamburg.freifunk.net | |
| − | Address = | ||
Cipher=blowfish | Cipher=blowfish | ||
Compression=0 | Compression=0 | ||
Digest=sha1 | Digest=sha1 | ||
IndirectData=no | IndirectData=no | ||
| − | |||
| − | |||
| − | |||
Port = 656 | Port = 656 | ||
-----BEGIN RSA PUBLIC KEY----- | -----BEGIN RSA PUBLIC KEY----- | ||
| Line 107: | Line 348: | ||
+7SgYW2/vAdnbFX689yKIs9inbQGNrakQQS/84pQ4TyN+H1dkhmxn5hweF/Ci3Qp | +7SgYW2/vAdnbFX689yKIs9inbQGNrakQQS/84pQ4TyN+H1dkhmxn5hweF/Ci3Qp | ||
UxzfjeVmeH2L+ecVOgWK10aoUhfVGvCVB3UpoCT6GrQwOa8gB5vfAgMBAAE= | UxzfjeVmeH2L+ecVOgWK10aoUhfVGvCVB3UpoCT6GrQwOa8gB5vfAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | ===== ffhh/hosts/elan ===== | ||
| + | Address = elan.ainex.net | ||
| + | Port = 656 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALHyO9nsCFXUSlvaBRHZX4DMFTg2xvVPx2Vhtv0NPKIFeSMRNJ1tfuTN | ||
| + | ZhFGT0yUpl2QdCf6Xm6k6gMyEIMgeRSNDTRmm/rgli7EnCA1wEIc30BFP7MHkzx7 | ||
| + | 1oYD/jQxJIWCyjW3kH1Ui3WkZHws8rvpALcicFSBgvCk7QzYq09nAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | |||
| + | ===== ffhh/hosts/lok72 ===== | ||
| + | Address=lok72.hamburg.freifunk.net | ||
| + | Cipher=blowfish | ||
| + | Compression=0 | ||
| + | Digest=sha1 | ||
| + | IndirectData=yes | ||
| + | Port=4300 | ||
| + | TCPonly=yes | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALMToovRzWqY6WOYdzQNz9FX5FbLj062qTgdIuds8eevezsSxRT8mFFL | ||
| + | s7j2nGw1rx9r54qouigJMMToP4hoSzq+wHHksQZoF9o3wrXfiRpQKdx0P5v3MERX | ||
| + | CpbV+r+AdZGWdCnNBAr4VbI0z3/gbC/yCKaqCXsRZrjwEeCfCSd9AgMBAAE= | ||
-----END RSA PUBLIC KEY----- | -----END RSA PUBLIC KEY----- | ||
| − | ==== | + | ===== ffhh/hosts/cgre ===== |
| + | Address = cgre.ath.cx | ||
| + | Port = 655 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAO19CddoFNDcmM8+WEv1AH6gDsexfLdd64puQlxqVbK9tfiBA2YCFD0X | ||
| + | K+bizO6yqMBwoBBJ8QyUsruUx+tJYeWJSfmuHmqJV4yUKqxiz0JObkqw0yuexQfj | ||
| + | hFUrj8XGFkJ/Q8sLJwr6W9CySK0BGDfQIArk/Zk1zOdU86UxHeupAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| − | ===== | + | ===== ffhh/hosts/Stockholm ===== |
| + | Address=Stockholm.hamburg.freifunk.net | ||
| + | Port=655 | ||
| + | TCPOnly = yes | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBANa5DF+Rsyd35eSbVR2+3TpEpeWFuDDAlVKBh63cbB744l7hPZ4lBJLq | ||
| + | lUugZ1Vg5PkpEB7teJ4g4jv6Dz3GI83KzQOqumbyYDesAvQdd9NNftsoSycApMPp | ||
| + | c+DLPxypZKpFET4Qb2uKc9ywo8DR/MFeottJVqehGYVrPj3IEaT7AgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| − | + | ===== ffhh/hosts/harburg1 ===== | |
| − | + | Address = harburg1.dyndns.org | |
| − | PrivateKeyFile = /etc/tinc/ | + | Port = 655 |
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAM59z1BuR6duHoSMqAFVrMpRSSrK/AAz5HCAcySaLzKJHgHJkJ/mTpiO | ||
| + | 5UR0U9+H2vhFfVqpzSyIgcNdqNJ+LMt8q1N38rSuxxaQ8nFxVzXxZwhjUgzzlo2H | ||
| + | IRJDfnYT0cHtCFF2xvDPyOvGkiCfKMjQ4Yieb/bmssMMKIpGAAbPAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | |||
| + | ==== InterCity VPN (icvpn) ==== | ||
| + | |||
| + | ===== icvpn/tinc.conf ===== | ||
| + | Name = hamburg11 | ||
| + | PrivateKeyFile = /etc/tinc/icvpn/rsa_key.priv | ||
Mode = Switch | Mode = Switch | ||
PingTimeout = 30 | PingTimeout = 30 | ||
#TCPOnly = yes | #TCPOnly = yes | ||
Port = 655 | Port = 655 | ||
| + | Hostnames=yes | ||
BindToAddress = 62.206.27.20 | BindToAddress = 62.206.27.20 | ||
| + | ConnectTo = hamburg2 | ||
| + | ConnectTo = berlin1 | ||
| + | ConnectTo = ffhallevpn1 | ||
| + | ConnectTo = erfurt1 | ||
| + | ConnectTo = erfurt2 | ||
| + | ConnectTo = leipzig1 | ||
| + | ConnectTo = leipzig2 | ||
| + | ConnectTo = aurich1 | ||
| + | ConnectTo = wien1 | ||
| + | ConnectTo = zagreb1 | ||
| + | ConnectTo = augsburg1 | ||
| + | ConnectTo = treuenbrietzen1 | ||
| − | ===== | + | ===== icvpn/tinc-up ===== |
| − | |||
#!/bin/sh | #!/bin/sh | ||
ip addr add dev $INTERFACE 10.207.0.9/16 broadcast 10.207.255.255 | ip addr add dev $INTERFACE 10.207.0.9/16 broadcast 10.207.255.255 | ||
ip link set dev $INTERFACE up | ip link set dev $INTERFACE up | ||
| + | iptables -A FORWARD -i ffhh -s 10.112.0.0/12 -o icvpn -j ACCEPT # FF Hamburg -> FF Global | ||
| − | ===== | + | ===== icvpn/tinc-down ===== |
| − | |||
#!/bin/sh | #!/bin/sh | ||
ip link set dev $INTERFACE down | ip link set dev $INTERFACE down | ||
ip addr del 10.207.0.9 dev $INTERFACE | ip addr del 10.207.0.9 dev $INTERFACE | ||
| + | iptables -D FORWARD -i ffhh -s 10.112.0.0/12 -o icvpn -j ACCEPT | ||
| − | |||
| − | + | ===== icvpn/hosts/hamburg1 ===== | |
| − | + | Address = vpn1.hamburg.freifunk.net | |
| − | |||
Port = 655 | Port = 655 | ||
-----BEGIN RSA PUBLIC KEY----- | -----BEGIN RSA PUBLIC KEY----- | ||
| Line 145: | Line 450: | ||
BZJEtmKjW+FrPRLTtJVeptlLWGJr+EE2/G3fq0/AbQDhzIT7OnqCNGrMC1YzNOZm | BZJEtmKjW+FrPRLTtJVeptlLWGJr+EE2/G3fq0/AbQDhzIT7OnqCNGrMC1YzNOZm | ||
C8CVyiPwELdvBL+Z7j6Jq545/1zZ/H+z1EK6xuucjhwITFqMQrdxAgMBAAE= | C8CVyiPwELdvBL+Z7j6Jq545/1zZ/H+z1EK6xuucjhwITFqMQrdxAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | ===== icvpn/hosts/hamburg2 ===== | ||
| + | Port = 656 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAKE101EjT+PGZOp8mqkscn7ZSB/82cdidJVtxm5g9fyH8S6cK4c/flC8 | ||
| + | 7Ye24uBv/qlajN9DBha6/Xdfzekg5GrqaAgyR2mkTKQNOWL72W3igDgas1YYgKZR | ||
| + | /bJoAJj1RHbSUaVCVVZKbmLMgwYtfB26zZ9ErnELKNnejPnk6lChAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/berlin1 ===== | ||
| + | address = vpn-ic1.berlin.freifunk.net | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALfEgQh1Po7B5/IP57pZT0iRjY+8GVfGgkYB7dFIANk/iSWjThe9pERm | ||
| + | x4GGx2NNoiNoDVdUtSz41oIc65bd651G01e2A1bnFQ9qRc9rZ/S91SqpO0+KheYw | ||
| + | judU2Mc81XkKQ38e9rgtU/OvWOF1Hq2EOOork2cePsC8QRa9oAa5AgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/ffhallevpn1 ===== | ||
| + | address = vpn1.freifunk-halle.de | ||
| + | address = 88.198.51.136 | ||
| + | Port = 655 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALF/Wu4pe+f3dHeLYApHxUnOGUBzpNREUet6nDp80uWT/dph7h6Yqtz2 | ||
| + | XMkifjDjSDnHPa1l1LwWFXkTKVQLH4lUrDuadXMU+BSEJWO36vg/A9E3AjbzoTA7 | ||
| + | RY6Gzx+FOXqTGOtqzEPMLkBGTrslerpw9JzfCgLlxLLCXg8Tri8ZAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/erfurt1 ===== | ||
| + | address = t35thr.dyndns.org | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAMB63H0OfUEUPoWPbM3tCCHQm+N9f8z0GDc7+fk+/8x09CuW6xmpfdm6 | ||
| + | vYrR6ceUsjRUhT/cIO6PhF3bUnaI7otAXHDSK4idvq99Z0miEvHWpJ9W0ZnbuUa4 | ||
| + | UeBJP0yCZLL4su7IPpdBWToPrgBHy43CAEnwdEHkp5iKE7zFscaPAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | ===== icvpn/hosts/erfurt2 ===== | ||
| + | Address = 195.190.142.204 | ||
| + | Port = 655 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALAoLEYO/u/V0qfnTiGgTD40RtWpQdh5YPy6kmBvkHJ0/WMAr2o1nGFg | ||
| + | FMJAQEMsiPp8LRLp3nsX9r0loW+sD5OMSe2zhR6rEo/e94x4tJxbSZr/5X52Kl+p | ||
| + | iKGoiDVeiv5zwbwS0CjKD2mVmHC7z95xzLe+DARTbpwMHbLiqAHlAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/leipzig1 ===== | ||
| + | Address = vpn1.leipzig.freifunk.net | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAKL7eWHmD2Rn6IP7JlSWtkphokN785g8nccBmfcjbwEwiZv+EFaVoid/ | ||
| + | 0dPfvHaX0GaQGOhpef3PVHEbIMuU8dD9+7WbXO3+hUSIAfHoIdGK7n8qFtzTpzqn | ||
| + | HAWcgneIE+sZVZRKC0B3VyQ8XujHuLCrQYkjRmVzvbb4cSzE+YhxAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/leipzig2 ===== | ||
| + | Address = vpn2.leipzig.freifunk.net | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALf6n7zN7GDf50k4F1+JbOde/7WGKc8HtaCNyIV93PeSFz1IiGpf8Vnn | ||
| + | 9xGl64X+5i07gH9l81Cx2/cgSqY3XYSTCVrCCaAJN5jnoQbubfQTojx/e0ZKDXeO | ||
| + | WVtjm6Y+TcqBLJ2TRAxmtyc3VX5VBfU3N3yaYZv3G+RzKNFI1VX7AgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/aurich1 ===== | ||
| + | Address = 217.7.143.189 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAMTmDsazE1oEcjoMdiVtRtRyY1YX13DtK7O3sYdNMUjQA1Zn+OgDPRxm | ||
| + | okwOAvT6ZqWr9xLmYWose3Vh7x4wuuNRuGaKgbB0bqWGWBlYeaqTTKGT9V/eJalj | ||
| + | n3of5UZQkTDpYHd4RWNRbYKT69sLfR4/8gmp4EUbAPD4JRBrUGPvAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/wien1 ===== | ||
| + | Address = 213.129.230.186 | ||
| + | Address = wien1.icvpn.funkfeuer.at | ||
| + | Address = 193.239.188.20 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAJ6ORemNoaEZLgCCvbHU3j3DA4+kKyVvZFPIs63MMQvCneazLs9Jc/bM | ||
| + | zmUo/TaApxHKIiLJU0TjbXGU/gT/ocSpmxgUGm66zwidYx+6HEOjAg0qnx5kuS/l | ||
| + | dmjVMsPBtStau9OBo79jaBalM2+P+bR7wqugFOWn5E9cV7iUouGrAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/zagreb1 ===== | ||
| + | Address = dugave-wireless.dnsalias.net | ||
| + | Subnet = 10.207.2.1 | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBAK+2pGmXfrTtp7vAPTwQgiTXTX7UH2QPiRMvBop2T6VzLHFCiHQW8PCs | ||
| + | jhZz4un7It4+JFn9hh/Srs04Unmt7useYM0smAWc0BVRjCMI8tMnlq8jlNXJ5+Ii | ||
| + | YMxEbo641maODYY40FYqBEXQ98wYpMHiCbeU+Vm/pfdK+qXBsY+HAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | |||
| + | ===== icvpn/hosts/augsburg1 ===== | ||
| + | Address = augsburg1.ath.cx | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBALVQaY0axASCewZdfMPbxUBwphhoDHKzm0SvpietNy0gy+43Jb+N/Cs+ | ||
| + | d9l9HlAS2ngrCAahVm/GRA3iYHH2i5JdZnzxPFKdkefcZFz7x0ZDaqeqpb2YLWFs | ||
| + | z2LPm37OCcsi9NPZtvDG+0Nas370xDn/6uZhCd0gAplDuI+3m0vRAgMBAAE= | ||
| + | -----END RSA PUBLIC KEY----- | ||
| + | |||
| + | ===== icvpn/hosts/treuenbrietzen1 ===== | ||
| + | Address = shonyt.mine.nu | ||
| + | -----BEGIN RSA PUBLIC KEY----- | ||
| + | MIGJAoGBANbR3LhhWFNt9ak//ZTReEuNQHjibgTAM+cNTDwLevudrP3y9htxTzgF | ||
| + | UZDHnkbDqwrYNjnuaMLIik7ljj5aKQd+fXmv3S+sFvvaPnm+e7Fpt+r/ReTnS6su | ||
| + | iOdmQ7XgC/b6r5ISjGhSheHcVSNMmbDWwYISSpDTu9S5qcUAkp1jAgMBAAE= | ||
-----END RSA PUBLIC KEY----- | -----END RSA PUBLIC KEY----- | ||
| Line 151: | Line 567: | ||
=== Quagga === | === Quagga === | ||
| − | + | ==== bgpd.conf ==== | |
| − | |||
| − | |||
! | ! | ||
| Line 159: | Line 573: | ||
! 2007/04/19 08:19:20 | ! 2007/04/19 08:19:20 | ||
! | ! | ||
| − | hostname | + | hostname bgpd@vpn1.hamburg.freifunk.net |
password 8 pophase | password 8 pophase | ||
enable password 8 blasehase | enable password 8 blasehase | ||
| + | log file /var/log/bgpd.log informational | ||
| + | log syslog informational | ||
service advanced-vty | service advanced-vty | ||
service password-encryption | service password-encryption | ||
| + | banner motd file /etc/issue.net | ||
! | ! | ||
| − | + | !debug bgp events | |
| − | |||
! | ! | ||
| − | + | bgp multiple-instance | |
! | ! | ||
router bgp 65044 | router bgp 65044 | ||
bgp router-id 10.207.0.9 | bgp router-id 10.207.0.9 | ||
bgp log-neighbor-changes | bgp log-neighbor-changes | ||
| + | bgp bestpath as-path confed | ||
| + | |||
| + | network 10.4.2.0/24 | ||
network 10.112.0.0/13 | network 10.112.0.0/13 | ||
network 10.120.0.0/14 | network 10.120.0.0/14 | ||
network 10.124.0.0/15 | network 10.124.0.0/15 | ||
network 10.126.0.0/16 | network 10.126.0.0/16 | ||
| − | + | ||
| − | + | neighbor ff-peers4 peer-group | |
| − | + | neighbor ff-peers4 update-source 10.207.0.9 | |
| − | + | neighbor ff-peers4 soft-reconfiguration inbound | |
| − | + | neighbor ff-peers4 prefix-list bgp4in in | |
| − | + | neighbor ff-peers4 prefix-list bgp4out out | |
| − | + | ||
| − | + | neighbor ff-peers6 peer-group | |
| − | + | neighbor ff-peers6 soft-reconfiguration inbound | |
| − | + | neighbor ff-peers6 prefix-list bgp6in in | |
| − | + | neighbor ff-peers6 prefix-list bgp6out out | |
| − | + | ||
| − | + | neighbor 10.207.0.1 remote-as 65041 | |
| − | + | neighbor 10.207.0.1 peer-group ff-peers4 | |
| − | + | neighbor 10.207.0.1 description Leipzig1 | |
| − | + | ||
| − | + | neighbor 10.207.0.2 remote-as 65041 | |
| − | + | neighbor 10.207.0.2 peer-group ff-peers4 | |
| − | + | neighbor 10.207.0.2 description Leipzig2 | |
| − | + | ||
| − | + | neighbor 10.207.0.3 remote-as 65042 | |
| − | + | neighbor 10.207.0.3 peer-group ff-peers4 | |
| − | + | neighbor 10.207.0.3 description Weimar1 | |
| − | + | ||
| − | + | neighbor 10.207.0.4 remote-as 65042 | |
| + | neighbor 10.207.0.4 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.4 description Weimar2 | ||
| + | |||
| + | neighbor 10.207.0.5 remote-as 65040 | ||
| + | neighbor 10.207.0.5 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.5 description Berlin1 | ||
| + | |||
| + | neighbor 10.207.0.6 remote-as 65040 | ||
| + | neighbor 10.207.0.6 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.6 description Berlin2 | ||
| + | |||
| + | neighbor 10.207.0.7 remote-as 65043 | ||
| + | neighbor 10.207.0.7 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.7 description Erfurt1 | ||
| + | |||
| + | neighbor 10.207.0.8 remote-as 65043 | ||
| + | neighbor 10.207.0.8 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.8 description Erfurt2 | ||
| + | |||
| + | neighbor 10.207.0.10 remote-as 65044 | ||
| + | neighbor 10.207.0.10 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.10 description Hamburg2 | ||
| + | |||
| + | neighbor 10.207.0.11 remote-as 65045 | ||
| + | neighbor 10.207.0.11 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.11 description Stuttgart1 | ||
| + | |||
| + | neighbor 10.207.0.12 remote-as 65045 | ||
| + | neighbor 10.207.0.12 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.12 description Stuttgart2 | ||
| + | |||
| + | neighbor 10.207.0.13 remote-as 65046 | ||
| + | neighbor 10.207.0.13 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.13 description Halle1 | ||
| + | |||
| + | neighbor 10.207.0.14 remote-as 65046 | ||
| + | neighbor 10.207.0.14 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.14 description Halle2 | ||
| + | |||
| + | neighbor 10.207.0.15 remote-as 65047 | ||
| + | neighbor 10.207.0.15 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.15 description Aurich1 | ||
| + | |||
| + | neighbor 10.207.0.16 remote-as 65048 | ||
| + | neighbor 10.207.0.16 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.16 description Chaos-Communication-Camp | ||
| + | |||
| + | neighbor 10.207.0.17 remote-as 65050 | ||
| + | neighbor 10.207.0.17 peer-group ff-peers4 | ||
| + | neighbor 10.207.0.17 description Ausgburg1 | ||
| + | |||
| + | neighbor 10.207.1.1 remote-as 35492 | ||
| + | neighbor 10.207.1.1 peer-group ff-peers4 | ||
| + | neighbor 10.207.1.1 description Wien1 | ||
| + | |||
| + | neighbor 10.207.1.2 remote-as 35492 | ||
| + | neighbor 10.207.1.2 peer-group ff-peers4 | ||
| + | neighbor 10.207.1.2 description Wien2 | ||
| + | |||
| + | neighbor 10.207.2.1 remote-as 65049 | ||
| + | neighbor 10.207.2.1 peer-group ff-peers4 | ||
| + | neighbor 10.207.2.1 description Zagreb1 | ||
| + | |||
| + | neighbor 10.207.255.1 remote-as 65041 | ||
| + | neighbor 10.207.255.1 peer-group ff-peers4 | ||
| + | neighbor 10.207.255.1 description Leipzig-FOO | ||
| + | |||
distance bgp 150 150 150 | distance bgp 150 150 150 | ||
| + | ! | ||
| + | address-family ipv6 | ||
| + | network 2001:6f8:982::/48 | ||
| + | network 2001:6f8:1300::/48 | ||
| + | network 2001:4830:1739::/48 | ||
| + | neighbor ff-peers6 activate | ||
| + | neighbor ff-peers6 soft-reconfiguration inbound | ||
| + | neighbor ff-peers6 prefix-list bgp6in in | ||
| + | neighbor ff-peers6 prefix-list bgp6out out | ||
| + | exit-address-family | ||
! | ! | ||
access-list access permit 127.0.0.1/32 | access-list access permit 127.0.0.1/32 | ||
| + | access-list access permit 10.35.2.8/32 | ||
| + | access-list access permit 10.35.3.0/24 | ||
| + | access-list access permit 172.31.0.0/24 | ||
access-list access deny any | access-list access deny any | ||
| − | + | ! | |
| − | + | ip prefix-list bgp4in description BGP IPv4 import filter | |
| − | access-list | + | ip prefix-list bgp4in seq 5 deny 0.0.0.0/8 le 32 |
| + | ip prefix-list bgp4in seq 10 deny 6.0.0.0/8 le 32 | ||
| + | ip prefix-list bgp4in seq 100 permit any | ||
| + | ! | ||
| + | ip prefix-list bgp4out description Out allowed routing announcements | ||
| + | ip prefix-list bgp4out seq 10 permit 10.112.0.0/12 le 32 | ||
| + | ip prefix-list bgp4out seq 20 permit 10.4.2.0/24 | ||
| + | ip prefix-list bgp4out seq 99 deny any | ||
| + | ! | ||
| + | ipv6 access-list access permit ::1/128 | ||
| + | ipv6 access-list access permit 2001:6f8:982::/48 | ||
| + | ipv6 access-list access permit 2001:6f8:1300::/48 | ||
| + | ipv6 access-list access permit 2001:4830:1739::/48 | ||
| + | ipv6 access-list access deny any | ||
| + | ! | ||
| + | ipv6 prefix-list bgp6in description BGP IPv6 import filter | ||
| + | ipv6 prefix-list bgp6in seq 5 deny ::/0 le 128 | ||
| + | ! | ||
| + | ipv6 prefix-list bgp6out description BGP IPv6 export filter | ||
| + | ipv6 prefix-list bgp6out seq 10 permit 2001:6f8:982::/48 le 64 | ||
| + | ipv6 prefix-list bgp6out seq 20 permit 2001:6f8:1300::/48 le 64 | ||
| + | ipv6 prefix-list bgp6out seq 99 deny any | ||
! | ! | ||
line vty | line vty | ||
access-class access | access-class access | ||
| + | ipv6 access-class access | ||
! | ! | ||
| + | end | ||
| + | |||
| + | |||
| + | ==== zebra.conf ==== | ||
| + | ! | ||
| + | ! Zebra configuration saved from vty | ||
| + | ! 2007/10/04 22:05:07 | ||
| + | ! | ||
| + | hostname zebra@vpn1.hamburg.freifunk.net | ||
| + | password 8 pophase | ||
| + | log file /var/log/zebra.log errors | ||
| + | log stdout | ||
| + | log syslog errors | ||
| + | service advanced-vty | ||
| + | service password-encryption | ||
| + | ! | ||
| + | interface eth0 | ||
| + | description LAN | ||
| + | bandwidth 100000 | ||
| + | link-detect | ||
| + | ipv6 nd suppress-ra | ||
| + | ! | ||
| + | interface eth1 | ||
| + | description Uplink-Telekom | ||
| + | bandwidth 1500 | ||
| + | link-detect | ||
| + | ip address 193.158.228.132/27 | ||
| + | ip address 195.243.248.60/29 | ||
| + | ipv6 address 2001:6f8:982:e2::1:1/128 | ||
| + | ipv6 address 2001:6f8:982:e2::2/64 | ||
| + | ipv6 nd suppress-ra | ||
| + | ! | ||
| + | interface eth2 | ||
| + | description Uplink-QSC-Broadnet | ||
| + | bandwidth 4000 | ||
| + | link-detect | ||
| + | ip address 62.206.27.20/26 | ||
| + | ipv6 address 2001:6f8:982:e1::1:1/128 | ||
| + | ipv6 address 2001:6f8:982:e1::2/64 | ||
| + | ipv6 address fec0::fc:bb:0:2/96 | ||
| + | ipv6 nd suppress-ra | ||
| + | ! | ||
| + | interface ffhh | ||
| + | description Freifunk-Hamburg | ||
| + | bandwidth 4000 | ||
| + | link-detect | ||
| + | ip address 10.112.1.1/12 | ||
| + | ipv6 address 2001:6f8:982:e3::1/64 | ||
| + | multicast | ||
| + | ipv6 nd suppress-ra | ||
| + | ipv6 nd prefix 2001:6f8:982:e3::/64 router-address | ||
| + | ! | ||
| + | interface icvpn | ||
| + | description Freifunk-InterCity-VPN | ||
| + | bandwidth 4000 | ||
| + | link-detect | ||
| + | ip address 10.207.0.9/16 | ||
| + | ipv6 address 2001:6f8:982:ffbb::1/128 | ||
| + | ipv6 address fec0::a:cf:0:9/96 | ||
| + | ipv6 nd suppress-ra | ||
| + | ! | ||
| + | interface lo | ||
| + | link-detect | ||
| + | ipv6 address ::1/128 | ||
| + | ! | ||
| + | interface sit0 | ||
| + | ipv6 nd suppress-ra | ||
| + | ! | ||
| + | ip route 62.206.43.0/24 62.206.27.1 | ||
| + | ip route 193.238.156.1/32 62.206.27.1 | ||
| + | ip route 195.243.248.56/29 eth1 | ||
| + | ipv6 route ::/0 2001:6f8:982:ffff::1 eth0 | ||
| + | ipv6 route 2001:6f8:982:9003::/64 2001:6f8:982:e3::2 ffhh | ||
| + | ! | ||
| + | access-list access permit 127.0.0.1/32 | ||
| + | access-list access deny any | ||
| + | ! | ||
| + | ipv6 access-list access permit ::1/128 | ||
| + | ipv6 access-list access permit 2001:6f8:982::/48 | ||
| + | ipv6 access-list access permit 2001:6f8:1300::/48 | ||
| + | ipv6 access-list access deny any | ||
| + | ! | ||
| + | router-id 172.31.0.251 | ||
| + | ip forwarding | ||
| + | ipv6 forwarding | ||
| + | ! | ||
| + | line vty | ||
| + | access-class access | ||
| + | ipv6 access-class access | ||
| + | ! | ||
| + | |||
| + | |||
| + | === n2n === | ||
| + | |||
| + | Auf diesem Knotenpunkt laeuft ein n2n-supernode, an den sich n2n Clients anbinden koennen. | ||
| + | |||
| + | Hostname : vpn1.hamburg.freifunk.net | ||
| + | Port : 4201 | ||
| + | Community : ffhh | ||
| + | Password : ffhh | ||
| + | |||
| + | Der Supernode Daemon wird ueber inittab respawnt, wenn der Prozess stirbt. Aus der /etc/inittab: | ||
| + | |||
| + | 7:23:respawn:/usr/bin/supernode -l 4201 -v &> /var/log/n2n-supernode.log | ||
| + | |||
| + | === l2gvpn === | ||
| + | |||
| + | Auf diesem Knotenpunkt laeuft ebenfalls ein l2gvpn Supernode und der dazugehoerige Client. | ||
| + | |||
| + | Hostname : vpn1.hamburg.freifunk.net | ||
| + | Port : 4204 | ||
| + | Community : ffhh | ||
| + | Password : ffhh | ||
| + | |||
| + | Sowohl Supernode, als auch Client werden ueber die /etc/inittab gestartet und respawnet, wenn der Prozess stirbt. Aus der /etc/inittab: | ||
| + | |||
| + | 8:23:respawn:/usr/local/sbin/l2gvpn-supernode vpn1 &> /var/log/l2gvpn-supernode.log | ||
| + | 9:23:respawn:/usr/local/sbin/l2gvpn-node ffhh &> /var/log/l2gvpn-node.log | ||
| + | |||
| + | Die dazugehoerige uci Konfiguration aus /etc/config/l2gvpn sieht wie folgt aus: | ||
| + | |||
| + | config 'supernode' 'vpn1' | ||
| + | option 'port' '4204' | ||
| + | |||
| + | config 'edge' 'ffhh' | ||
| + | option 'mac' '00:11:22:33:44:55' | ||
| + | option 'community' 'ffhh' | ||
| + | option 'key' 'ffhh' | ||
| + | option 'port' '7666' | ||
| + | option 'supernode' '127.0.0.1:4204' | ||
| + | option 'tundev' 'ffhh_l2gvpn' | ||
| + | option 'netmask' '255.240.0.0' | ||
| + | option 'ipaddr' '10.112.43.2' | ||
| + | option 'subnet' '255.240.0.0' | ||
| + | |||
| + | config 'l2gvpn' 'debug' | ||
| + | option 'headers' '1' | ||
| + | option 'verbose' '4' | ||
| + | |||
| + | === Sonstiges === | ||
| + | |||
| + | ==== /etc/issue.net ==== | ||
| + | |||
| + | ,----------------------------------------------------------------------. | ||
| + | | | | ||
| + | | Unauthorized use of this system is prohibited and may be prosecuted | | ||
| + | | to the fullest extent of law. By using this system, you implicitly | | ||
| + | | agree to monitoring by system management and law enforcement | | ||
| + | | authorities. If you do not agree with these terms, | | ||
| + | | DISCONNECT NOW! | | ||
| + | | ;-p | | ||
| + | `----------------------------------------------------------------------^ | ||
| + | |||
| + | |||
| + | [[Category:Freifunk]] | ||
Latest revision as of 22:22, 27 November 2012
Der Inhalt dieser Seite ist veraltet. Wenn du etwas neues hinzufügen kannst, sei mutig!
Dieser Node besteht momentan aus einer virtuellen Maschine unter VMware ESXi und soll die Verbindung zwischen den einzelnen Funkwolken in Hamburg und Freifunk Initiativen in anderen Staedten herstellen. Als VPN Software wird Tinc-VPN, OpenVPN und n2n eingesetzt. Eine kleine Hilfestellung fuer die VPN Konfiguration auf Basis von OpenWRT kann man hier finden: Freifunk:IP:VPN_Connect
Es gibt ein Looking Glass im Hamburger Freifunk Netz, das allerdings auch nur aus dem Freifunk Netz erreichbar ist: http://lg.hamburg.freifunk.net/
Contents
- 1 Interfaces
- 2 Konfigurationen
- 2.1 OLSRd
- 2.2 Tinc-VPN
- 2.2.1 Hamburger Freifunk VPN (ffhh)
- 2.2.2 InterCity VPN (icvpn)
- 2.2.2.1 icvpn/tinc.conf
- 2.2.2.2 icvpn/tinc-up
- 2.2.2.3 icvpn/tinc-down
- 2.2.2.4 icvpn/hosts/hamburg1
- 2.2.2.5 icvpn/hosts/hamburg2
- 2.2.2.6 icvpn/hosts/berlin1
- 2.2.2.7 icvpn/hosts/ffhallevpn1
- 2.2.2.8 icvpn/hosts/erfurt1
- 2.2.2.9 icvpn/hosts/erfurt2
- 2.2.2.10 icvpn/hosts/leipzig1
- 2.2.2.11 icvpn/hosts/leipzig2
- 2.2.2.12 icvpn/hosts/aurich1
- 2.2.2.13 icvpn/hosts/wien1
- 2.2.2.14 icvpn/hosts/zagreb1
- 2.2.2.15 icvpn/hosts/augsburg1
- 2.2.2.16 icvpn/hosts/treuenbrietzen1
- 2.3 Quagga
- 2.4 n2n
- 2.5 l2gvpn
- 2.6 Sonstiges
Interfaces
Hier eine kurze Uebersicht ueber die verschiedenen Netzwerk-Interfaces.
eth0
Das eth0 Interface ist momentan noch ungenutzt.
Interface Name: eth0 IP Adresse : 62.206.43.20 Hostname : vpn1.hamburg.freifunk.net Description : uplink Bandwidth : 10mbit up/down
ffhh_tinc
Dieses Interface ist fuer das Hamburger Freifunk Netz eingerichtet. Tinc-VPN setzt dieses Interface in den TAP-Modus, damit Pakete zwischen den einzelnen VPN Clients wie bei einem Switch verschickt werden koennen. Die OLSR und B.A.T.M.A.N. Daemons senden ihre Pakete an die Broadcast-Adresse (10.127.255.255) ueber dieses Interface.
Interface Name: ffhh_tinc IP Adresse : 10.112.1.1/12 Hostname : none Description : Freifunk Hamburg Software : tinc-vpn, olsrd Tinc-Port : 656
ffhh_ovpn
Interface Name: ffhh_ovpn IP Adresse : 10.112.1.3/12 Hostname : none Description : Freifunk Hamburg Software : openvpn, olsrd OpenVPN-Port : 4223
ffhh_n2n
Interface Name: ffhh_tinc IP Adresse : 10.112.1.4/12 Hostname : none Description : Freifunk Hamburg Software : n2n, olsrd
icvpn
Fuer das InterCity-VPN wurde dieses Interface eingerichtet. Tinc-VPN setzt auch dieses Interface in den TAP-Modus und die Quagga Routing Suite kuendigt den Hamburger Freifunk IP-Bereich an entfernte BGP-Router. Wir verwenden die interne AS-Nummer 65044 fuer das BGP-Peering.
Interface Name: icvpn IP Adresse : 10.207.0.9/16 Hostname : none Description : tunnel staedtekopplung Software : tinc-vpn, quagga(bgpd) Tinc-Port : 655 AS-Number : 65044
Konfigurationen
OLSRd
/etc/olsrd-ipv4.conf
DebugLevel 2
IpVersion 4
FIBMetric "flat"
ClearScreen yes
AllowNoInt yes
Hna4
{
0.0.0.0 0.0.0.0 # Default Route to Internet
10.112.1.255 255.255.255.255 # Looking Glass IP Address
10.207.0.0 255.255.0.0 # ICVPN Transfer Network
10.4.0.0 255.252.0.0 # CCC Hamburg ChaosVPN
10.32.0.0 255.240.0.0 # CCC Hamburg ChaosVPN
77.87.48.0 255.255.248.0 # Freifunk Berlin public IP range
191.161.0.0 255.255.0.0 # Freifunk Augsburg
194.26.180.0 255.255.255.0 # Freifunk Erfurt
10.2.0.0 255.255.0.0 # Freifunk Hannover
10.12.0.0 255.255.0.0 # Freifunk Dresden
10.200.0.0 255.255.0.0 # Freifunk Dresden
172.22.0.0 255.254.0.0 # dn42.net (aka diac24.net)
104.0.0.0 255.0.0.0 # BerlinBackBone OLSR Range
105.0.0.0 255.0.0.0 # BerlinBackBone Batman Range
10.35.0.0 255.255.0.0 # FCruise Hamburg Datacenter
91.210.212.0 255.255.255.240 # FCruise Hamburg Transfer Network
91.210.215.0 255.255.255.0 # FCruise Hamburg testing network
}
# TOS(type of service) value for
# the IP header of control traffic.
# If not set it will default to 16
#TosValue 16
# The fixed willingness to use(0-7)
# If not set willingness will be calculated
# dynamically based on battery/power status
# if such information is available
#Willingness 4
# Allow processes like the GUI front-end
# to connect to the daemon.
IpcConnect
{
MaxConnections 0
Host 127.0.0.1
#Net 192.168.1.0 255.255.255.0
}
UseHysteresis no
#HystScaling 0.50
#HystThrHigh 0.80
#HystThrLow 0.30
LinkQualityLevel 2
#LinkQualityAging 0.1
#LinkQualityAlgorithm "etx_fpm"
Pollrate 0.05
NicChgsPollInt 3.0
# TC redundancy
# Specifies how much neighbor info should
# be sent in TC messages
# Possible values are:
# 0 - only send MPR selectors
# 1 - send MPR selectors and MPRs
# 2 - send all neighbors
#
# defaults to 0
TcRedundancy 2
#
# MPR coverage
# Specifies how many MPRs a node should
# try select to reach every 2 hop neighbor
#
# Can be set to any integer >0
#
# defaults to 1
MprCoverage 3
# Olsrd plugins to load
# This must be the absolute path to the file
# or the loader will use the following scheme:
# - Try the paths in the LD_LIBRARY_PATH
# environment variable.
# - The list of libraries cached in /etc/ld.so.cache
# - /lib, followed by /usr/lib
# Example plugin entry with parameters:
LoadPlugin "olsrd_dot_draw.so.0.3"
{
PlParam "port" "2004"
PlParam "allow" "127.0.0.1"
PlParam "allow" "localhost"
}
LoadPlugin "olsrd_httpinfo.so.0.1"
{
PlParam "port" "8080"
PlParam "net" "0.0.0.0 0.0.0.0"
}
Interface "ffhh_tinc" "ffhh_ovpn" "ffhh_n2n"
{
Ip4Broadcast 255.255.255.255
HelloInterval 2.0
HelloValidityTime 20.0
TcInterval 5.0
TcValidityTime 30.0
MidInterval 5.0
MidValidityTime 30.0
HnaInterval 5.0
HnaValidityTime 30.0
}
Interface "n2n"
{
Ip4Broadcast 255.255.255.255
HelloInterval '50.0'
HelloValidityTime '900.0'
TcInterval '30.0'
TcValidityTime '2700.0'
MidInterval '150.0'
MidValidityTime '2700.0'
HnaInterval '150.0'
HnaValidityTime '900.0'
}
/etc/olsrd-ipv6.conf
DebugLevel 2
IpVersion 6
AllowNoInt yes
Pollrate 0.025
TcRedundancy 2
MprCoverage 3
LinkQualityFishEye 1
LinkQualityWinSize 100
LinkQualityDijkstraLimit 0 9.0
LinkQualityLevel 2
UseHysteresis no
FIBMetric "flat"
ClearScreen yes
Willingness 3
LinkQualityAging 0.1
#LinkQualityAlgorithm "etx_fpm"
LinkQualityAlgorithm "etx_ff"
Hna6
{
:: 0 # Announce Default Gateway
2002:3ece:2b14:: 48 # Announce 6to4 prefix
0:0:0:0:0:FFFF:0:0 96 # Announce siit prefix
0:0:0:0:0:FFFF:0A70:0101 125 # Announce siit 10.112.1.0-7
}
IpcConnect
{
MaxConnections 0
Host 127.0.0.1
#Net 192.168.1.0 255.255.255.0
}
NicChgsPollInt 3.0
LoadPlugin "olsrd_dot_draw.so.0.3"
{
PlParam "port" "2006"
PlParam "allow" "127.0.0.1"
PlParam "allow" "localhost"
}
Interface "ffhh_tinc" "ffhh_ovpn" "ffhh_n2n"
{
Ip6AddrType global
Ip6MulticastGlobal ff0e::1
HelloInterval 2.0
HelloValidityTime 40.0
TcInterval 5.0
TcValidityTime 100.0
MidInterval 18.0
MidValidityTime 324.0
HnaInterval 18.0
HnaValidityTime 108.0
}
Interface "n2n"
{
Ip6AddrType global
Ip6MulticastGlobal ff0e::1
HelloInterval '50.0'
HelloValidityTime '900.0'
TcInterval '30.0'
TcValidityTime '2700.0'
MidInterval '150.0'
MidValidityTime '2700.0'
HnaInterval '150.0'
HnaValidityTime '900.0'
}
Tinc-VPN
Hamburger Freifunk VPN (ffhh)
ffhh/tinc.conf
AddressFamily=ipv4 Name = vpn1 PrivateKeyFile = /etc/tinc/ffhh/rsa_key.priv Mode = Switch PingTimeout = 30 Port = 656 BindToAddress = 62.206.27.20 Hostnames=yes ConnectTo = lok72 ConnectTo = elan ConnectTo = harburg1 #ConnectTo = vpn2 #ConnectTo = cgre #ConnectTo = Stockholm
ffhh/tinc-up
#!/bin/sh ip addr add dev $INTERFACE 10.112.1.1/12 broadcast 10.127.255.255 ip link set dev $INTERFACE up
ffhh/tinc-down
#!/bin/sh ip link set dev $INTERFACE down ip addr del 10.112.1.1 dev $INTERFACE
ffhh/hosts/vpn1
Address = vpn1.hamburg.freifunk.net Cipher=blowfish Compression=0 Digest=sha1 IndirectData=no Port = 656 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAKVI9lNEiJ3JVDuXhsLKdqhE+k14bCM8cYaAReNrzBSDODxuLm+pPKwo +7SgYW2/vAdnbFX689yKIs9inbQGNrakQQS/84pQ4TyN+H1dkhmxn5hweF/Ci3Qp UxzfjeVmeH2L+ecVOgWK10aoUhfVGvCVB3UpoCT6GrQwOa8gB5vfAgMBAAE= -----END RSA PUBLIC KEY-----
ffhh/hosts/elan
Address = elan.ainex.net Port = 656 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALHyO9nsCFXUSlvaBRHZX4DMFTg2xvVPx2Vhtv0NPKIFeSMRNJ1tfuTN ZhFGT0yUpl2QdCf6Xm6k6gMyEIMgeRSNDTRmm/rgli7EnCA1wEIc30BFP7MHkzx7 1oYD/jQxJIWCyjW3kH1Ui3WkZHws8rvpALcicFSBgvCk7QzYq09nAgMBAAE= -----END RSA PUBLIC KEY-----
ffhh/hosts/lok72
Address=lok72.hamburg.freifunk.net Cipher=blowfish Compression=0 Digest=sha1 IndirectData=yes Port=4300 TCPonly=yes -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALMToovRzWqY6WOYdzQNz9FX5FbLj062qTgdIuds8eevezsSxRT8mFFL s7j2nGw1rx9r54qouigJMMToP4hoSzq+wHHksQZoF9o3wrXfiRpQKdx0P5v3MERX CpbV+r+AdZGWdCnNBAr4VbI0z3/gbC/yCKaqCXsRZrjwEeCfCSd9AgMBAAE= -----END RSA PUBLIC KEY-----
ffhh/hosts/cgre
Address = cgre.ath.cx Port = 655 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAO19CddoFNDcmM8+WEv1AH6gDsexfLdd64puQlxqVbK9tfiBA2YCFD0X K+bizO6yqMBwoBBJ8QyUsruUx+tJYeWJSfmuHmqJV4yUKqxiz0JObkqw0yuexQfj hFUrj8XGFkJ/Q8sLJwr6W9CySK0BGDfQIArk/Zk1zOdU86UxHeupAgMBAAE= -----END RSA PUBLIC KEY-----
ffhh/hosts/Stockholm
Address=Stockholm.hamburg.freifunk.net Port=655 TCPOnly = yes -----BEGIN RSA PUBLIC KEY----- MIGJAoGBANa5DF+Rsyd35eSbVR2+3TpEpeWFuDDAlVKBh63cbB744l7hPZ4lBJLq lUugZ1Vg5PkpEB7teJ4g4jv6Dz3GI83KzQOqumbyYDesAvQdd9NNftsoSycApMPp c+DLPxypZKpFET4Qb2uKc9ywo8DR/MFeottJVqehGYVrPj3IEaT7AgMBAAE= -----END RSA PUBLIC KEY-----
ffhh/hosts/harburg1
Address = harburg1.dyndns.org Port = 655 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAM59z1BuR6duHoSMqAFVrMpRSSrK/AAz5HCAcySaLzKJHgHJkJ/mTpiO 5UR0U9+H2vhFfVqpzSyIgcNdqNJ+LMt8q1N38rSuxxaQ8nFxVzXxZwhjUgzzlo2H IRJDfnYT0cHtCFF2xvDPyOvGkiCfKMjQ4Yieb/bmssMMKIpGAAbPAgMBAAE= -----END RSA PUBLIC KEY-----
InterCity VPN (icvpn)
icvpn/tinc.conf
Name = hamburg11 PrivateKeyFile = /etc/tinc/icvpn/rsa_key.priv Mode = Switch PingTimeout = 30 #TCPOnly = yes Port = 655 Hostnames=yes BindToAddress = 62.206.27.20 ConnectTo = hamburg2 ConnectTo = berlin1 ConnectTo = ffhallevpn1 ConnectTo = erfurt1 ConnectTo = erfurt2 ConnectTo = leipzig1 ConnectTo = leipzig2 ConnectTo = aurich1 ConnectTo = wien1 ConnectTo = zagreb1 ConnectTo = augsburg1 ConnectTo = treuenbrietzen1
icvpn/tinc-up
#!/bin/sh ip addr add dev $INTERFACE 10.207.0.9/16 broadcast 10.207.255.255 ip link set dev $INTERFACE up iptables -A FORWARD -i ffhh -s 10.112.0.0/12 -o icvpn -j ACCEPT # FF Hamburg -> FF Global
icvpn/tinc-down
#!/bin/sh ip link set dev $INTERFACE down ip addr del 10.207.0.9 dev $INTERFACE iptables -D FORWARD -i ffhh -s 10.112.0.0/12 -o icvpn -j ACCEPT
icvpn/hosts/hamburg1
Address = vpn1.hamburg.freifunk.net Port = 655 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAL5ld4OnWv52XD8q0MbfW+DLUe2lCaHLyf4XacwqOhjvS5RH+iAyPgIc BZJEtmKjW+FrPRLTtJVeptlLWGJr+EE2/G3fq0/AbQDhzIT7OnqCNGrMC1YzNOZm C8CVyiPwELdvBL+Z7j6Jq545/1zZ/H+z1EK6xuucjhwITFqMQrdxAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/hamburg2
Port = 656 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAKE101EjT+PGZOp8mqkscn7ZSB/82cdidJVtxm5g9fyH8S6cK4c/flC8 7Ye24uBv/qlajN9DBha6/Xdfzekg5GrqaAgyR2mkTKQNOWL72W3igDgas1YYgKZR /bJoAJj1RHbSUaVCVVZKbmLMgwYtfB26zZ9ErnELKNnejPnk6lChAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/berlin1
address = vpn-ic1.berlin.freifunk.net -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALfEgQh1Po7B5/IP57pZT0iRjY+8GVfGgkYB7dFIANk/iSWjThe9pERm x4GGx2NNoiNoDVdUtSz41oIc65bd651G01e2A1bnFQ9qRc9rZ/S91SqpO0+KheYw judU2Mc81XkKQ38e9rgtU/OvWOF1Hq2EOOork2cePsC8QRa9oAa5AgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/ffhallevpn1
address = vpn1.freifunk-halle.de address = 88.198.51.136 Port = 655 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALF/Wu4pe+f3dHeLYApHxUnOGUBzpNREUet6nDp80uWT/dph7h6Yqtz2 XMkifjDjSDnHPa1l1LwWFXkTKVQLH4lUrDuadXMU+BSEJWO36vg/A9E3AjbzoTA7 RY6Gzx+FOXqTGOtqzEPMLkBGTrslerpw9JzfCgLlxLLCXg8Tri8ZAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/erfurt1
address = t35thr.dyndns.org -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAMB63H0OfUEUPoWPbM3tCCHQm+N9f8z0GDc7+fk+/8x09CuW6xmpfdm6 vYrR6ceUsjRUhT/cIO6PhF3bUnaI7otAXHDSK4idvq99Z0miEvHWpJ9W0ZnbuUa4 UeBJP0yCZLL4su7IPpdBWToPrgBHy43CAEnwdEHkp5iKE7zFscaPAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/erfurt2
Address = 195.190.142.204 Port = 655 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALAoLEYO/u/V0qfnTiGgTD40RtWpQdh5YPy6kmBvkHJ0/WMAr2o1nGFg FMJAQEMsiPp8LRLp3nsX9r0loW+sD5OMSe2zhR6rEo/e94x4tJxbSZr/5X52Kl+p iKGoiDVeiv5zwbwS0CjKD2mVmHC7z95xzLe+DARTbpwMHbLiqAHlAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/leipzig1
Address = vpn1.leipzig.freifunk.net -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAKL7eWHmD2Rn6IP7JlSWtkphokN785g8nccBmfcjbwEwiZv+EFaVoid/ 0dPfvHaX0GaQGOhpef3PVHEbIMuU8dD9+7WbXO3+hUSIAfHoIdGK7n8qFtzTpzqn HAWcgneIE+sZVZRKC0B3VyQ8XujHuLCrQYkjRmVzvbb4cSzE+YhxAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/leipzig2
Address = vpn2.leipzig.freifunk.net -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALf6n7zN7GDf50k4F1+JbOde/7WGKc8HtaCNyIV93PeSFz1IiGpf8Vnn 9xGl64X+5i07gH9l81Cx2/cgSqY3XYSTCVrCCaAJN5jnoQbubfQTojx/e0ZKDXeO WVtjm6Y+TcqBLJ2TRAxmtyc3VX5VBfU3N3yaYZv3G+RzKNFI1VX7AgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/aurich1
Address = 217.7.143.189 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAMTmDsazE1oEcjoMdiVtRtRyY1YX13DtK7O3sYdNMUjQA1Zn+OgDPRxm okwOAvT6ZqWr9xLmYWose3Vh7x4wuuNRuGaKgbB0bqWGWBlYeaqTTKGT9V/eJalj n3of5UZQkTDpYHd4RWNRbYKT69sLfR4/8gmp4EUbAPD4JRBrUGPvAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/wien1
Address = 213.129.230.186 Address = wien1.icvpn.funkfeuer.at Address = 193.239.188.20 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAJ6ORemNoaEZLgCCvbHU3j3DA4+kKyVvZFPIs63MMQvCneazLs9Jc/bM zmUo/TaApxHKIiLJU0TjbXGU/gT/ocSpmxgUGm66zwidYx+6HEOjAg0qnx5kuS/l dmjVMsPBtStau9OBo79jaBalM2+P+bR7wqugFOWn5E9cV7iUouGrAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/zagreb1
Address = dugave-wireless.dnsalias.net Subnet = 10.207.2.1 -----BEGIN RSA PUBLIC KEY----- MIGJAoGBAK+2pGmXfrTtp7vAPTwQgiTXTX7UH2QPiRMvBop2T6VzLHFCiHQW8PCs jhZz4un7It4+JFn9hh/Srs04Unmt7useYM0smAWc0BVRjCMI8tMnlq8jlNXJ5+Ii YMxEbo641maODYY40FYqBEXQ98wYpMHiCbeU+Vm/pfdK+qXBsY+HAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/augsburg1
Address = augsburg1.ath.cx -----BEGIN RSA PUBLIC KEY----- MIGJAoGBALVQaY0axASCewZdfMPbxUBwphhoDHKzm0SvpietNy0gy+43Jb+N/Cs+ d9l9HlAS2ngrCAahVm/GRA3iYHH2i5JdZnzxPFKdkefcZFz7x0ZDaqeqpb2YLWFs z2LPm37OCcsi9NPZtvDG+0Nas370xDn/6uZhCd0gAplDuI+3m0vRAgMBAAE= -----END RSA PUBLIC KEY-----
icvpn/hosts/treuenbrietzen1
Address = shonyt.mine.nu -----BEGIN RSA PUBLIC KEY----- MIGJAoGBANbR3LhhWFNt9ak//ZTReEuNQHjibgTAM+cNTDwLevudrP3y9htxTzgF UZDHnkbDqwrYNjnuaMLIik7ljj5aKQd+fXmv3S+sFvvaPnm+e7Fpt+r/ReTnS6su iOdmQ7XgC/b6r5ISjGhSheHcVSNMmbDWwYISSpDTu9S5qcUAkp1jAgMBAAE= -----END RSA PUBLIC KEY-----
Quagga
bgpd.conf
! ! Zebra configuration saved from vty ! 2007/04/19 08:19:20 ! hostname bgpd@vpn1.hamburg.freifunk.net password 8 pophase enable password 8 blasehase log file /var/log/bgpd.log informational log syslog informational service advanced-vty service password-encryption banner motd file /etc/issue.net ! !debug bgp events ! bgp multiple-instance ! router bgp 65044 bgp router-id 10.207.0.9 bgp log-neighbor-changes bgp bestpath as-path confed network 10.4.2.0/24 network 10.112.0.0/13 network 10.120.0.0/14 network 10.124.0.0/15 network 10.126.0.0/16 neighbor ff-peers4 peer-group neighbor ff-peers4 update-source 10.207.0.9 neighbor ff-peers4 soft-reconfiguration inbound neighbor ff-peers4 prefix-list bgp4in in neighbor ff-peers4 prefix-list bgp4out out neighbor ff-peers6 peer-group neighbor ff-peers6 soft-reconfiguration inbound neighbor ff-peers6 prefix-list bgp6in in neighbor ff-peers6 prefix-list bgp6out out neighbor 10.207.0.1 remote-as 65041 neighbor 10.207.0.1 peer-group ff-peers4 neighbor 10.207.0.1 description Leipzig1 neighbor 10.207.0.2 remote-as 65041 neighbor 10.207.0.2 peer-group ff-peers4 neighbor 10.207.0.2 description Leipzig2 neighbor 10.207.0.3 remote-as 65042 neighbor 10.207.0.3 peer-group ff-peers4 neighbor 10.207.0.3 description Weimar1 neighbor 10.207.0.4 remote-as 65042 neighbor 10.207.0.4 peer-group ff-peers4 neighbor 10.207.0.4 description Weimar2 neighbor 10.207.0.5 remote-as 65040 neighbor 10.207.0.5 peer-group ff-peers4 neighbor 10.207.0.5 description Berlin1 neighbor 10.207.0.6 remote-as 65040 neighbor 10.207.0.6 peer-group ff-peers4 neighbor 10.207.0.6 description Berlin2 neighbor 10.207.0.7 remote-as 65043 neighbor 10.207.0.7 peer-group ff-peers4 neighbor 10.207.0.7 description Erfurt1 neighbor 10.207.0.8 remote-as 65043 neighbor 10.207.0.8 peer-group ff-peers4 neighbor 10.207.0.8 description Erfurt2 neighbor 10.207.0.10 remote-as 65044 neighbor 10.207.0.10 peer-group ff-peers4 neighbor 10.207.0.10 description Hamburg2 neighbor 10.207.0.11 remote-as 65045 neighbor 10.207.0.11 peer-group ff-peers4 neighbor 10.207.0.11 description Stuttgart1 neighbor 10.207.0.12 remote-as 65045 neighbor 10.207.0.12 peer-group ff-peers4 neighbor 10.207.0.12 description Stuttgart2 neighbor 10.207.0.13 remote-as 65046 neighbor 10.207.0.13 peer-group ff-peers4 neighbor 10.207.0.13 description Halle1 neighbor 10.207.0.14 remote-as 65046 neighbor 10.207.0.14 peer-group ff-peers4 neighbor 10.207.0.14 description Halle2 neighbor 10.207.0.15 remote-as 65047 neighbor 10.207.0.15 peer-group ff-peers4 neighbor 10.207.0.15 description Aurich1 neighbor 10.207.0.16 remote-as 65048 neighbor 10.207.0.16 peer-group ff-peers4 neighbor 10.207.0.16 description Chaos-Communication-Camp neighbor 10.207.0.17 remote-as 65050 neighbor 10.207.0.17 peer-group ff-peers4 neighbor 10.207.0.17 description Ausgburg1 neighbor 10.207.1.1 remote-as 35492 neighbor 10.207.1.1 peer-group ff-peers4 neighbor 10.207.1.1 description Wien1 neighbor 10.207.1.2 remote-as 35492 neighbor 10.207.1.2 peer-group ff-peers4 neighbor 10.207.1.2 description Wien2 neighbor 10.207.2.1 remote-as 65049 neighbor 10.207.2.1 peer-group ff-peers4 neighbor 10.207.2.1 description Zagreb1 neighbor 10.207.255.1 remote-as 65041 neighbor 10.207.255.1 peer-group ff-peers4 neighbor 10.207.255.1 description Leipzig-FOO distance bgp 150 150 150 ! address-family ipv6 network 2001:6f8:982::/48 network 2001:6f8:1300::/48 network 2001:4830:1739::/48 neighbor ff-peers6 activate neighbor ff-peers6 soft-reconfiguration inbound neighbor ff-peers6 prefix-list bgp6in in neighbor ff-peers6 prefix-list bgp6out out exit-address-family ! access-list access permit 127.0.0.1/32 access-list access permit 10.35.2.8/32 access-list access permit 10.35.3.0/24 access-list access permit 172.31.0.0/24 access-list access deny any ! ip prefix-list bgp4in description BGP IPv4 import filter ip prefix-list bgp4in seq 5 deny 0.0.0.0/8 le 32 ip prefix-list bgp4in seq 10 deny 6.0.0.0/8 le 32 ip prefix-list bgp4in seq 100 permit any ! ip prefix-list bgp4out description Out allowed routing announcements ip prefix-list bgp4out seq 10 permit 10.112.0.0/12 le 32 ip prefix-list bgp4out seq 20 permit 10.4.2.0/24 ip prefix-list bgp4out seq 99 deny any ! ipv6 access-list access permit ::1/128 ipv6 access-list access permit 2001:6f8:982::/48 ipv6 access-list access permit 2001:6f8:1300::/48 ipv6 access-list access permit 2001:4830:1739::/48 ipv6 access-list access deny any ! ipv6 prefix-list bgp6in description BGP IPv6 import filter ipv6 prefix-list bgp6in seq 5 deny ::/0 le 128 ! ipv6 prefix-list bgp6out description BGP IPv6 export filter ipv6 prefix-list bgp6out seq 10 permit 2001:6f8:982::/48 le 64 ipv6 prefix-list bgp6out seq 20 permit 2001:6f8:1300::/48 le 64 ipv6 prefix-list bgp6out seq 99 deny any ! line vty access-class access ipv6 access-class access ! end
zebra.conf
! ! Zebra configuration saved from vty ! 2007/10/04 22:05:07 ! hostname zebra@vpn1.hamburg.freifunk.net password 8 pophase log file /var/log/zebra.log errors log stdout log syslog errors service advanced-vty service password-encryption ! interface eth0 description LAN bandwidth 100000 link-detect ipv6 nd suppress-ra ! interface eth1 description Uplink-Telekom bandwidth 1500 link-detect ip address 193.158.228.132/27 ip address 195.243.248.60/29 ipv6 address 2001:6f8:982:e2::1:1/128 ipv6 address 2001:6f8:982:e2::2/64 ipv6 nd suppress-ra ! interface eth2 description Uplink-QSC-Broadnet bandwidth 4000 link-detect ip address 62.206.27.20/26 ipv6 address 2001:6f8:982:e1::1:1/128 ipv6 address 2001:6f8:982:e1::2/64 ipv6 address fec0::fc:bb:0:2/96 ipv6 nd suppress-ra ! interface ffhh description Freifunk-Hamburg bandwidth 4000 link-detect ip address 10.112.1.1/12 ipv6 address 2001:6f8:982:e3::1/64 multicast ipv6 nd suppress-ra ipv6 nd prefix 2001:6f8:982:e3::/64 router-address ! interface icvpn description Freifunk-InterCity-VPN bandwidth 4000 link-detect ip address 10.207.0.9/16 ipv6 address 2001:6f8:982:ffbb::1/128 ipv6 address fec0::a:cf:0:9/96 ipv6 nd suppress-ra ! interface lo link-detect ipv6 address ::1/128 ! interface sit0 ipv6 nd suppress-ra ! ip route 62.206.43.0/24 62.206.27.1 ip route 193.238.156.1/32 62.206.27.1 ip route 195.243.248.56/29 eth1 ipv6 route ::/0 2001:6f8:982:ffff::1 eth0 ipv6 route 2001:6f8:982:9003::/64 2001:6f8:982:e3::2 ffhh ! access-list access permit 127.0.0.1/32 access-list access deny any ! ipv6 access-list access permit ::1/128 ipv6 access-list access permit 2001:6f8:982::/48 ipv6 access-list access permit 2001:6f8:1300::/48 ipv6 access-list access deny any ! router-id 172.31.0.251 ip forwarding ipv6 forwarding ! line vty access-class access ipv6 access-class access !
n2n
Auf diesem Knotenpunkt laeuft ein n2n-supernode, an den sich n2n Clients anbinden koennen.
Hostname : vpn1.hamburg.freifunk.net Port : 4201 Community : ffhh Password : ffhh
Der Supernode Daemon wird ueber inittab respawnt, wenn der Prozess stirbt. Aus der /etc/inittab:
7:23:respawn:/usr/bin/supernode -l 4201 -v &> /var/log/n2n-supernode.log
l2gvpn
Auf diesem Knotenpunkt laeuft ebenfalls ein l2gvpn Supernode und der dazugehoerige Client.
Hostname : vpn1.hamburg.freifunk.net Port : 4204 Community : ffhh Password : ffhh
Sowohl Supernode, als auch Client werden ueber die /etc/inittab gestartet und respawnet, wenn der Prozess stirbt. Aus der /etc/inittab:
8:23:respawn:/usr/local/sbin/l2gvpn-supernode vpn1 &> /var/log/l2gvpn-supernode.log 9:23:respawn:/usr/local/sbin/l2gvpn-node ffhh &> /var/log/l2gvpn-node.log
Die dazugehoerige uci Konfiguration aus /etc/config/l2gvpn sieht wie folgt aus:
config 'supernode' 'vpn1' option 'port' '4204' config 'edge' 'ffhh' option 'mac' '00:11:22:33:44:55' option 'community' 'ffhh' option 'key' 'ffhh' option 'port' '7666' option 'supernode' '127.0.0.1:4204' option 'tundev' 'ffhh_l2gvpn' option 'netmask' '255.240.0.0' option 'ipaddr' '10.112.43.2' option 'subnet' '255.240.0.0' config 'l2gvpn' 'debug' option 'headers' '1' option 'verbose' '4'
Sonstiges
/etc/issue.net
,----------------------------------------------------------------------. | | | Unauthorized use of this system is prohibited and may be prosecuted | | to the fullest extent of law. By using this system, you implicitly | | agree to monitoring by system management and law enforcement | | authorities. If you do not agree with these terms, | | DISCONNECT NOW! | | ;-p | `----------------------------------------------------------------------^